SSL Certificate

The most common and widely known use of SSL/TLS is secure web browsing via the HTTPS protocol. A properly configured public HTTPS website includes an SSL/TLS certificate signed by a trusted Certificate Authority (CA). Users visiting HTTPS websites can rest assured:
Authenticity: The server presenting the certificate possesses the private key matching the public key in the certificate.
Integrity: Signed documents (e.g., web pages) have not been altered by intermediaries during transmission.
Communication between the client and server is encrypted.
Due to these properties, SSL/TLS and HTTPS allow users to securely transmit confidential information over the Internet, such as credit card numbers, social security numbers, and login credentials, while ensuring they are sent to genuine websites. On insecure HTTP websites, this data is sent in plaintext, accessible to any eavesdropper intercepting the data flow. Moreover, users of unprotected websites lack trusted third-party verification that the site they are visiting is indeed what it claims to be.
- Security Identification -
SSL Certificate Encryption
SSL certificate encryption ensures robust security to protect your clients. All communications between you and your site visitors are fully safeguarded. For technical personnel, this means SHA-256 and 2048-bit RSA key support, along with Elliptic Curve Cryptography (ECC).

Make Customers Feel Secure
To assure customers of their safety, SSL encryption displays seals from the world’s largest certificate authorities on your website, alongside browser padlocks indicating protection. SSL earns invaluable customer trust.
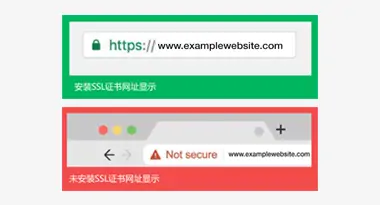
Improve SEO Rankings
Google flags non-SSL sites as "Not Secure" and ranks SSL-enabled sites higher in search results. Considering this, "SSL" holds immense significance, as losing customers carries high costs.
- Types of SSL Certificates -
All certificates offer the same encryption level; the difference lies in the validation process required to obtain them and their visual indicators in the browser address bar. Encryption hides communications from hackers but cannot prevent them from intercepting and impersonating your site to steal customer data. As consumers shift from physical stores to online shopping and banking, they must trust they are visiting genuine merchant websites—something difficult to prove online. Based on validation rigor, SSL certificates are categorized into Extended Validation (EV SSL), Organization Validation (OV SSL), and Domain Validation (DV SSL).

- Data Protection -
Their primary purpose is securing communication between clients and servers. Thus, all information is encrypted via SSL certificate installation. In practice, this data is locked, accessible only to browsers or servers with decryption keys. SSL technology enables handling sensitive data—passwords, credit card numbers, and IDs—without vulnerabilities from malicious proxies.
- How They Work -
When you enter sensitive data on an SSL-certified website, it is automatically encrypted and accessible only to the applicant. With encryption key protection, even if intercepted by hackers, your data remains unreadable to malicious actors. Crucially, SSL certificates also verify users access legitimate sites, not phishing pages. The padlock icon next to the URL assures safe site access and operations—a vital feature for business platforms.

- Conventional SSL Certificate Application Process -
After domain or public IP confirmation, submit to the Certificate Authority (CA) for validation. Identity-verified SSL certificates also authenticate users, providing online safety assurances. This is critical in the digital landscape rife with scams, as the tool confirms whom users communicate with before data transmission to fake sites.
During SSL installation, users undergo a Certificate Authority (CA) verification process, which not only grants access to trusted indicators but also validates their and their company’s identity. Post-verification, installation is time-consuming; errors require rework, reducing efficiency.
Multilingual subdomains necessitate multiple purchases and reinstallations, hindering rapid website launches!

