- EasyOperate Experience Test: Deployment Cycle, Stability, and Post-Sale Evaluation2025-12-17View details
- Guide to Choosing a Foreign Trade Website System: How to Evaluate Multilingual Website Capabilities2025-12-17View details
- From the perspective of quality control and security, experience the use of EasyStore: vulnerabilities, backups, and permission management2025-12-17View details
- Foreign Trade Marketing System in Action: 5 Key Configuration Points to Enhance Overseas Lead Conversion2025-12-17View details
- How to Choose a Smart Website Building Platform for Distributors: Recommended Smart Website Platforms and Profit-Sharing Models2025-12-17View details
- Complete Breakdown of Foreign Trade Independent Website Construction Solutions: 7 Key Steps from Selection to Launch That Project Managers Must Know2025-12-16View details
- Comparison of SaaS Costs for Foreign Trade Independent Websites: How was the annual 30,000 website construction plan selected?2025-12-17View details
- Comparison of SaaS Costs for Foreign Trade Independent Websites: How was the annual 30,000 website construction plan selected?2025-12-17View details
From the perspective of quality control and security, experience the use of EasyStore: vulnerabilities, backups, and permission management
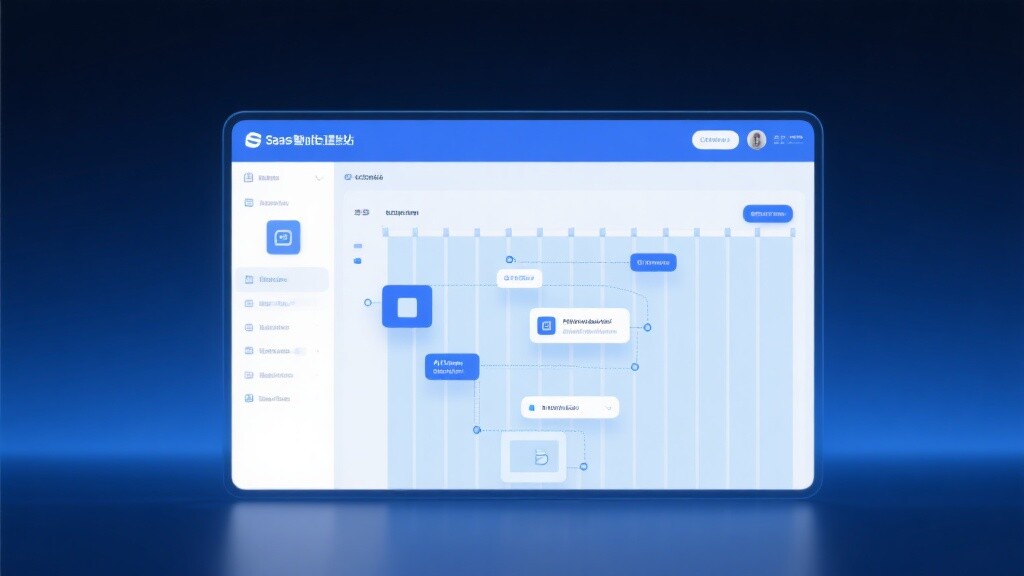
From the perspective of quality control and security, this in-depth evaluation of EasyYunbao's user experience focuses on analyzing vulnerability risks, backup mechanisms, and permission management to assist in technology assessment and procurement decisions. This article targets users and operators, technology evaluators, procurement personnel, enterprise decision-makers, and quality control and security management personnel, concentrating on the three most critical dimensions in actual operation scenarios and providing actionable recommendations. The evaluation unfolds along three main lines: functional delivery, operational observability, and compliance, combined with intelligent website platform competitive product analysis and industry standards, offering practical references for foreign trade website systems and global multilingual website implementation to facilitate more precise decision-making in EasyYunbao competitive product comparisons.
1. Vulnerability Risk Identification and Continuous Detection Capabilities

In internet service environments, vulnerability management is the primary factor in assessing platform security. For AI-driven all-in-one intelligent marketing platforms like EasyYunbao, attention must be paid to three layers of vulnerability exposure points: application-layer plugin and template security, third-party API and ad placement interface access control, and potential input validation issues introduced by multilingual rendering and translation engines. Procurement personnel are advised to prioritize extracting static code scanning and dynamic penetration test reports during intelligent website platform competitive analysis, while verifying version lifecycle management records of third-party dependencies and requiring suppliers to provide SLA security incident lists and response time data from the past three months. The operations team should employ real-time threat intelligence and baseline comparisons, adopting an automated vulnerability scanning combined with manual review model to reduce false positives and missed reports. In foreign trade marketing system scenarios, special testing is required for multilingual forms and right-to-left text rendering input filtering rules to prevent cross-site scripting or template injection leading to data leakage risks.
2. Backup Strategies and Disaster Recovery Drills
Stable backup mechanisms are core to ensuring business continuity. When evaluating EasyYunbao's user experience, focus should be on backup granularity, frequency, and cross-region recovery capabilities, as these three factors collectively determine recovery point objectives (RPO) and recovery time objectives (RTO). For global multilingual websites and foreign trade website system scenarios, a layered backup strategy is recommended: static resources and media should use CDN mirroring and versioned object storage; databases and configurations should combine incremental backups with daily full backups, storing backups in at least two geographically isolated regions to address single-point availability zone failures. Procurement and quality control personnel should request monthly recovery drill records from the past year and verify end-to-end recovery processes from backup to online restoration, including DNS failover, SSL certificate reissuance, and third-party service coordination, confirming whether actual RTO and RPO meet business requirements through drills. For Middle East market-oriented industry websites, verify the completeness of right-to-left layout template recovery, including localized translation and ad keyword optimization metadata restoration integrity. For specialized solutions targeting Middle Eastern clients, refer to product examples like Arabic Industry Website Construction and Marketing Solutions and verify their first-year maintenance services and Arabic keyword optimization implementation support.
3. Permission Management and Least Privilege Practices
Permission management directly impacts internal and external risk exposure. For enterprise procurement and technology evaluation teams, assessment should cover four dimensions: identity authentication, multi-factor authentication, least privilege, and audit trails. Priority should be given to verifying whether the platform supports role-based access control (RBAC) and attribute-based fine-grained strategies, and whether tenant isolation and sub-account permission delegation can be achieved in reseller and distributor models, with support for time-bound and temporary authorization to meet post-sales maintenance scenarios under the principle of least privilege. Security management personnel should inspect permission change audit trails and chains, ensuring login and operation logs comply with regulatory requirements and integrating with SIEM or log management platforms for abnormal behavior alerts. Additionally, when integrating third-party ad platforms like Google Ads and Meta, evaluate OAuth authorization lifecycle management, support for permission revocation and minimal scope authorization, avoiding long-term open tokens leading to account overreach, ad cost失控, or data leakage. Implementation recommendations include regular permission reviews, establishing permission approval workflows and automated expiration回收 strategies, and incorporating these requirements into procurement contracts and SLA clauses.

4. Monitoring and Observability: Incident Response and Operational Closed Loop
Effective monitoring and observability can shift quality control forward, capturing potential issues before users perceive them. When evaluating EasyYunbao's monitoring system, start from four indicator categories: performance monitoring, log collection, security posture, and business metrics, confirming whether the platform provides real-time site availability detection, multilingual site loading performance indicators, compliant SSL certificate auto-renewal, and CDN origin health checks. Technology evaluators should request demonstrations of abnormal traffic detection and DDoS protection capabilities, as well as ad channel traffic anomaly alert strategies, verifying in ad intelligence manager modules whether AI diagnostic tools can provide interpretable optimization suggestions and support historical comparative analysis to judge real effects before and after ad changes. Operations and post-sales maintenance teams need to jointly develop incident response manuals with suppliers, including classification standards, notification chains, and cross-team collaboration workflows, conducting periodic tabletop exercises to ensure rapid recovery and minimal loss during actual incidents. For distributors and agents, transparent multi-tenant monitoring dashboards and permission isolation are key elements supporting standardized replication.
Conclusion and Action Guidance
In summary, evaluating EasyYunbao's user experience from quality control and security perspectives should comprehensively consider four dimensions: vulnerability management, backup and disaster strategies, granular permission controls, and observability with incident response. In EasyYunbao competitive comparisons and intelligent website platform analyses, procurement teams are advised to formalize the above checkpoints into evaluation matrices and stipulate drills and SLA indicators in contracts to ensure long-term stable operation of foreign trade website systems and global multilingual websites. EasyYunbao, combining proprietary AI with global edge deployment, has clear advantages in performance and traffic ecosystems, while purchasers should adhere to security and compliance-first principles to steadily advance in rapid overseas expansion and localized marketing. For further understanding of Middle East market localization deployments and Arabic keyword optimization solutions, or to obtain demonstration implementation plans and quotes, please contact us immediately to learn more about solutions and schedule technology evaluation meetings.
- Website Construction
- Platform
- Foreign Trade Website
- SSL Certificate
- Google Ads
- Keyword Optimization
- Campbell (name)
- Intelligent website building
- Global multilingual website
- Foreign Trade Website System
- Foreign Trade Marketing System
- Smart Website Platform
- Easy Treasure User Experience
- 智能建站平台竞品分析
- EasyStore product competition comparison
- Multilingual Website
Related Articles
Related Products